SBOM, or Software Bill of Materials, is a critical component in today’s complex software landscape. Imagine a detailed recipe for your software, listing every ingredient (component) and its source. This inventory not only reveals the building blocks of your application but also helps you understand potential vulnerabilities and risks within your software supply chain.
Table of Contents
SBOMs provide a comprehensive snapshot of the software, including libraries, frameworks, and dependencies. This information is crucial for identifying and mitigating security threats, managing licenses, and ensuring compliance with regulations. By understanding the composition of your software, you gain valuable insights into its security posture, potential risks, and overall health.
What is an SBOM?
An SBOM, or Software Bill of Materials, is a comprehensive list of all the software components used in a piece of software. It’s like a recipe for a software application, detailing all the ingredients (software components) needed to build it.
The purpose of an SBOM is to provide transparency and visibility into the software supply chain. It helps organizations understand the components used in their software, identify potential vulnerabilities, and manage risks associated with those components.
Examples of SBOM Use
SBOMs are becoming increasingly important in various industries due to the growing complexity of software and the increasing number of cyberattacks. Here are some examples of how SBOMs are used:
- Software Security: SBOMs help organizations identify and mitigate vulnerabilities in their software by providing a detailed list of all the components used. This information can be used to patch known vulnerabilities or to avoid using components with known security issues.
- License Compliance: SBOMs can help organizations ensure compliance with software licensing requirements by identifying all the components used in their software and their associated licenses. This can help organizations avoid legal issues related to software licensing.
- Supply Chain Management: SBOMs can help organizations manage their software supply chains by providing a comprehensive inventory of all the components used in their software. This information can be used to track the origin of components, identify potential risks, and manage dependencies.
Components of an SBOM
An SBOM (Software Bill of Materials) is a structured document that lists the components of a software system, along with their versions and dependencies. It acts as a comprehensive inventory, providing insights into the software’s composition.
Elements of an SBOM
The elements included in an SBOM provide a detailed picture of the software’s structure and dependencies. This information is crucial for various tasks, including vulnerability management, license compliance, and security audits.
- Component Name: This element identifies the specific software component, such as a library, framework, or tool. It provides a unique identifier for each component, facilitating accurate tracking and analysis. For example, a component name could be “Apache HTTP Server” or “jQuery.”
- Version: This element specifies the exact version of the component used in the software. Version information is critical for understanding potential vulnerabilities and ensuring compatibility with other components. For example, a component version could be “2.4.53” or “3.6.1.”
- Dependencies: This element Artikels the relationships between different components in the software. It lists the components that are required for a specific component to function correctly. Dependencies can be direct or indirect, and understanding these relationships is vital for managing vulnerabilities and ensuring software stability. For example, a component might depend on a specific version of a database library or a particular operating system.
- Source: This element indicates the origin of the component. It might specify the repository, website, or package manager where the component was obtained. This information helps trace the component’s lineage and identify potential risks associated with its origin. For example, a component’s source could be “GitHub” or “npm.”
- License: This element details the licensing terms associated with the component. It specifies the rights and restrictions regarding the use, modification, and distribution of the component. License information is essential for ensuring compliance with legal requirements and avoiding potential copyright infringements. For example, a component’s license could be “Apache 2.0” or “MIT.”
- Hash: This element provides a unique cryptographic fingerprint of the component. It acts as a digital signature, verifying the integrity and authenticity of the component. Hash values are used to detect any unauthorized modifications or tampering with the component. For example, a component’s hash could be a SHA-256 value like “c3a46787130424169562f537703409122704371769399e506210653926970207.”
Format and Structure of an SBOM
The format and structure of an SBOM can significantly impact its usability and effectiveness. A well-structured SBOM is easy to understand, analyze, and process, while a poorly structured one can lead to confusion and errors. Common formats for SBOMs include:
- CycloneDX: This format is widely used for SBOMs, providing a comprehensive and standardized structure. It is supported by various tools and platforms, making it a versatile option. CycloneDX uses a JSON or XML format for representing the SBOM data.
- SPDX: This format is also popular for SBOMs, offering a flexible and extensible structure. It supports various data elements and allows for customization, making it suitable for diverse use cases. SPDX uses a JSON or XML format for representing the SBOM data.
- SWID Tag: This format is specifically designed for software identification, providing a concise and standardized way to represent software components. It is often used in conjunction with other formats, such as CycloneDX or SPDX. SWID Tag uses an XML format for representing the SBOM data.
Benefits of Using SBOMs
SBOMs offer significant advantages in managing software security and supply chain risks. By providing a comprehensive inventory of components, they empower organizations to understand their software’s composition and identify potential vulnerabilities.
Enhanced Security
SBOMs provide a detailed inventory of software components, enabling organizations to identify and address vulnerabilities. This proactive approach strengthens security by:
- Identifying known vulnerabilities: By comparing SBOMs with vulnerability databases, organizations can quickly identify components with known security flaws. This allows for timely patching and mitigation, reducing the risk of exploitation.
- Detecting malicious components: SBOMs help detect malicious or compromised components within software. This includes identifying components from untrusted sources or those with known security risks.
- Improving incident response: In the event of a security incident, SBOMs facilitate rapid investigation and remediation. By understanding the affected components, organizations can isolate the issue and implement necessary countermeasures efficiently.
Improved Software Supply Chain Risk Management
SBOMs play a crucial role in managing risks throughout the software supply chain by:
- Visibility and Transparency: SBOMs provide transparency into the software supply chain, allowing organizations to understand the origin and dependencies of their components. This visibility helps identify potential risks and vulnerabilities early on.
- Risk Assessment and Mitigation: By analyzing SBOMs, organizations can assess the risk associated with individual components and prioritize mitigation efforts. This includes evaluating the security posture of component providers and implementing appropriate controls.
- Improved Communication and Collaboration: SBOMs facilitate effective communication and collaboration between stakeholders in the software supply chain. They enable sharing of component information, vulnerability alerts, and mitigation strategies.
Compliance with Regulations and Industry Standards
SBOMs are becoming increasingly essential for compliance with regulations and industry standards, including:
- Executive Order 14028: This order requires federal agencies to use SBOMs for all software they develop or acquire. It aims to enhance software security and supply chain resilience.
- NIST Cybersecurity Framework (CSF): The CSF emphasizes the importance of software supply chain risk management, and SBOMs are considered a critical component in achieving this objective.
- National Vulnerability Database (NVD): The NVD uses SBOMs to identify and prioritize vulnerabilities in software components. Organizations are encouraged to use SBOMs to align with NVD recommendations.
Creating an SBOM
Creating an SBOM is essential for understanding and managing the software supply chain. It provides a comprehensive inventory of all the components used in a software product, enabling organizations to identify vulnerabilities, manage licenses, and track dependencies. There are various methods and tools available to create SBOMs, each with its advantages and disadvantages.
Methods for Creating an SBOM
There are several methods for creating an SBOM, each with its own strengths and weaknesses. The most common methods include:
- Manual creation: This involves manually identifying and documenting all the components in a software product. While this method provides the most control over the SBOM’s content, it can be time-consuming and error-prone, especially for complex software projects.
- Automated tools: Many tools are available to automate the SBOM creation process. These tools can analyze source code, package managers, and build systems to generate SBOMs. Automated tools are faster and more efficient than manual creation, but they may not always capture all the components, especially if the software uses custom libraries or dependencies.
- Hybrid approach: This combines manual and automated methods to create an SBOM. It leverages automated tools to capture the majority of components and then manually reviews and completes the SBOM. This approach offers a balance between accuracy and efficiency.
Tools and Technologies for SBOM Generation
Several tools and technologies can be used to generate SBOMs. These tools can be categorized into three main types:
- Static analysis tools: These tools analyze source code to identify dependencies and components. Examples include:
- Snyk: A popular static analysis tool that can generate SBOMs and identify vulnerabilities.
- Sonatype Nexus Lifecycle: A comprehensive software supply chain management platform that includes SBOM generation capabilities.
- JFrog Xray: Another widely used tool for SBOM generation and vulnerability management.
- Package managers: These tools are used to manage software packages and can also generate SBOMs. Examples include:
- npm: The package manager for Node.js, which can generate an SBOM using the `npm ls` command.
- Maven: The build tool for Java projects, which can generate an SBOM using the `mvn dependency:tree` command.
- pip: The package manager for Python, which can generate an SBOM using the `pip freeze` command.
- Build systems: These tools are used to automate the software build process and can also generate SBOMs. Examples include:
- Jenkins: A popular continuous integration and continuous delivery (CI/CD) server that can generate SBOMs using plugins.
- GitHub Actions: A CI/CD platform that can generate SBOMs using the `actions/create-sbom` action.
- Azure DevOps: A cloud-based CI/CD platform that can generate SBOMs using the `Azure DevOps Build` tasks.
Best Practices for Creating SBOMs
Creating accurate and comprehensive SBOMs is crucial for effective software supply chain management. Here are some best practices to follow:
- Use a standardized format: Choose a standardized format for your SBOMs, such as SPDX (Software Package Data Exchange) or CycloneDX. This ensures that the SBOMs are easily shared and understood by different tools and systems.
- Include all components: Ensure that your SBOM includes all components used in your software, including direct and transitive dependencies. This provides a complete picture of the software’s composition.
- Use a consistent methodology: Develop a consistent methodology for creating SBOMs across your organization. This ensures that all SBOMs are created using the same process and standards, making them more reliable and comparable.
- Automate the process: Automate the SBOM creation process as much as possible to reduce manual effort and ensure accuracy.
- Regularly update SBOMs: Update your SBOMs regularly to reflect any changes in the software’s composition. This is especially important after software updates or upgrades.
- Store SBOMs securely: Store your SBOMs securely to protect them from unauthorized access and modification.
- Share SBOMs with stakeholders: Share your SBOMs with relevant stakeholders, such as developers, security teams, and legal teams. This enables them to understand the software’s composition and take appropriate actions.
Using an SBOM
An SBOM can be a powerful tool for improving software security and managing software dependencies. By providing a comprehensive inventory of the components that make up a software application, an SBOM enables organizations to identify and address vulnerabilities, track software licenses, and manage software dependencies more effectively.
Identifying and Mitigating Vulnerabilities
SBOMs can help identify and mitigate vulnerabilities by providing a clear picture of the components that make up a software application. This information can be used to identify known vulnerabilities in the components and to take steps to mitigate those vulnerabilities.
For example, if an SBOM reveals that a software application uses a component with a known vulnerability, the organization can take steps to update the component or to implement other security measures to protect against the vulnerability.
- Vulnerability Scanning: SBOMs can be used to automate vulnerability scanning by providing a list of components that need to be scanned. This can save time and effort compared to manually scanning each component.
- Patch Management: SBOMs can be used to track the patches that have been applied to the components of a software application. This information can be used to ensure that all components are up-to-date and that any known vulnerabilities have been patched.
- Risk Assessment: SBOMs can be used to assess the risk of vulnerabilities in a software application. This information can be used to prioritize security efforts and to focus on the most critical vulnerabilities.
Tracking Software Dependencies and Managing Software Licenses
SBOMs can help track software dependencies and manage software licenses by providing a clear picture of the components that make up a software application and their associated licenses. This information can be used to identify and manage potential license compliance issues.
- Dependency Management: SBOMs can be used to identify and manage software dependencies. This information can be used to ensure that all dependencies are compatible with each other and with the software application.
- License Compliance: SBOMs can be used to track the licenses of the components that make up a software application. This information can be used to ensure that the software application is compliant with all applicable licensing requirements.
- Open Source Software Management: SBOMs can be used to manage the use of open source software in a software application. This information can be used to identify and manage potential legal and security risks associated with the use of open source software.
Integrating SBOMs into Existing Software Development Workflows
SBOMs can be integrated into existing software development workflows to improve security and compliance. This can be done by incorporating SBOM generation into the build process and by using SBOMs to inform security testing and vulnerability management activities.
- Continuous Integration/Continuous Delivery (CI/CD): SBOMs can be integrated into CI/CD pipelines to automate the generation and analysis of SBOMs. This can help to ensure that SBOMs are created and updated regularly.
- Security Testing: SBOMs can be used to inform security testing by providing a list of components that need to be tested. This can help to ensure that security testing is comprehensive and effective.
- Vulnerability Management: SBOMs can be used to support vulnerability management by providing a list of components that are vulnerable. This information can be used to prioritize vulnerability remediation efforts.
SBOM Standards and Formats
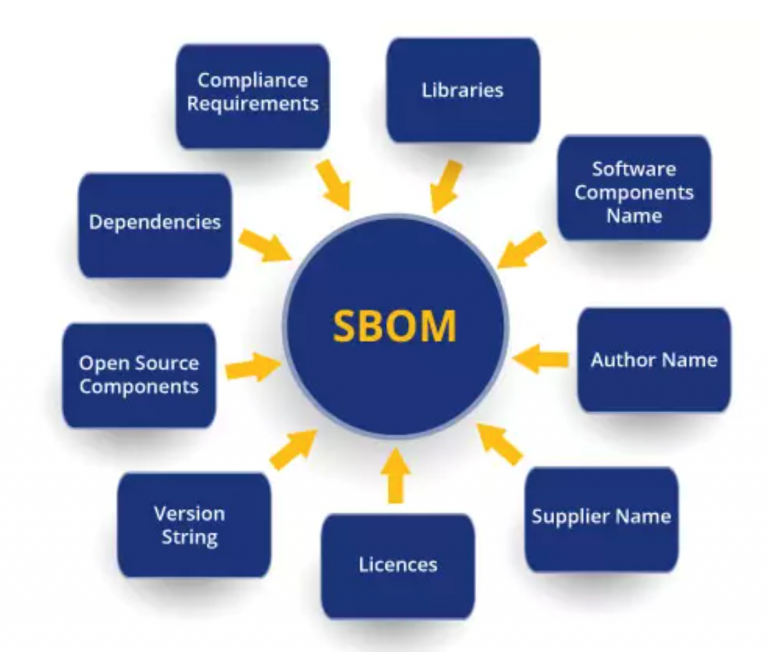
SBOM standards and formats are essential for ensuring the interoperability and usability of SBOMs. Different standards and formats offer varying levels of detail, structure, and flexibility, each with its own advantages and disadvantages.
SBOM Standards
Different SBOM standards provide frameworks for defining the structure and content of an SBOM. These standards aim to promote consistency and facilitate the exchange of SBOMs between different tools and systems.
- SPDX (Software Package Data Exchange) is a widely adopted open standard that defines a common language and data model for describing software components. SPDX is a comprehensive standard that includes information about licenses, copyrights, security vulnerabilities, and other relevant metadata.
- CycloneDX is another popular open standard that focuses on providing a lightweight and machine-readable format for SBOMs. CycloneDX is designed to be easily parsed and used by automated tools.
- SWID (Software Identification) is a standard developed by the National Institute of Standards and Technology (NIST) for uniquely identifying software components. SWID tags are used to identify software components and track their distribution.
- OWASP CycloneDX is a standard for describing software components and their relationships in a machine-readable format. It is designed to be easily parsed and used by automated tools.
- National Vulnerability Database (NVD) is a comprehensive database of publicly known cybersecurity vulnerabilities. It includes information about vulnerabilities, their impact, and potential solutions.
SBOM Formats
SBOMs can be represented in different formats, each with its own strengths and weaknesses.
- JSON (JavaScript Object Notation) is a lightweight and human-readable format that is commonly used for data exchange. JSON is a versatile format that can be easily parsed and used by automated tools.
- XML (Extensible Markup Language) is a hierarchical data format that is widely used for representing structured data. XML is a powerful format that can be used to represent complex data structures.
- CSV (Comma-Separated Values) is a simple and widely used format for representing tabular data. CSV is a good choice for representing simple SBOMs that contain basic information about software components.
- YAML (YAML Ain’t Markup Language) is a human-readable data serialization language that is commonly used for configuration files and data exchange. YAML is a flexible format that is easy to read and write.
Advantages and Disadvantages of SBOM Standards and Formats
The choice of SBOM standard and format can significantly impact the usability and interoperability of SBOMs.
- Advantages of Standardized SBOMs:
- Improved interoperability between different tools and systems.
- Increased transparency and accountability in the software supply chain.
- Enhanced security by enabling the identification and mitigation of vulnerabilities.
- Simplified compliance with regulations and industry standards.
- Disadvantages of Standardized SBOMs:
- Potential for complexity and overhead in creating and managing SBOMs.
- Limited flexibility in representing specialized or non-standard software components.
- Possible challenges in integrating SBOMs with legacy systems.
Impact of Standard Choice on SBOM Usability and Interoperability
The choice of SBOM standard and format can significantly impact the usability and interoperability of SBOMs.
- Usability: A well-defined and standardized SBOM format can make it easier for users to understand and interpret the information contained in an SBOM.
- Interoperability: A standardized SBOM format can ensure that SBOMs can be easily exchanged between different tools and systems.
The Future of SBOMs
The use of SBOMs is rapidly expanding, driven by evolving regulations and a growing awareness of the importance of software supply chain security. As we move forward, we can expect to see SBOMs playing an increasingly crucial role in shaping the software development landscape.
Emerging Trends in SBOM Use
SBOMs are becoming more prevalent in various aspects of the software development lifecycle. Here are some key trends:
- Integration with DevSecOps: SBOMs are being integrated into DevSecOps pipelines, enabling automated vulnerability scanning and risk assessment throughout the development process.
- Real-time SBOM Generation: Tools are emerging that generate SBOMs in real-time, providing up-to-date insights into the software’s composition and dependencies.
- SBOM Sharing and Collaboration: Platforms are being developed to facilitate the sharing and collaboration of SBOMs, enabling better coordination and visibility across the software supply chain.
- SBOM Standardization: Efforts are underway to standardize SBOM formats and data models, ensuring interoperability and seamless integration across different tools and platforms.
Applications Beyond Software Security
While SBOMs are primarily associated with software security, their applications extend beyond vulnerability management.
- License Compliance: SBOMs can help organizations comply with software licensing requirements by providing detailed information about the licenses used in their software.
- Software Composition Analysis: SBOMs can facilitate software composition analysis, enabling developers to identify and manage technical debt, optimize code, and improve maintainability.
- Software Evolution and Maintenance: SBOMs can provide valuable insights into the evolution of software, aiding in software migration, modernization, and long-term maintenance efforts.
- Software Ecosystem Analysis: SBOMs can be used to analyze the broader software ecosystem, identifying trends, dependencies, and potential risks.
Vision for the Future of SBOMs
The future of SBOMs holds immense potential for transforming the software development ecosystem.
- SBOMs as a Fundamental Software Artifact: SBOMs will become an integral part of software development, considered a fundamental artifact alongside source code and documentation.
- SBOMs as a Key Enabler of Software Trust: SBOMs will play a pivotal role in establishing trust in software, enabling organizations to confidently use and rely on software components.
- SBOMs Driving Innovation: SBOMs will foster innovation by providing a foundation for new tools and services that enhance software security, compliance, and collaboration.
SBOMs and Software Supply Chain Security
SBOMs play a crucial role in strengthening software supply chain security by providing a comprehensive inventory of software components used in an application. This detailed information enables organizations to better understand the risks associated with their software supply chain and take proactive steps to mitigate potential vulnerabilities.
Identifying and Mitigating Vulnerabilities
SBOMs help identify and mitigate vulnerabilities in third-party components by providing a clear picture of the components used in an application. With this information, organizations can:
- Identify vulnerable components: By comparing the SBOM with known vulnerability databases, organizations can quickly identify components that have known security flaws.
- Prioritize remediation efforts: SBOMs help organizations prioritize remediation efforts by highlighting the most critical vulnerabilities based on their severity and impact.
- Track component updates: SBOMs allow organizations to track component updates and ensure that they are using the latest secure versions.
Improving Transparency and Accountability
SBOMs contribute to a more transparent and accountable software supply chain by providing a clear record of the components used in an application. This transparency enables:
- Increased trust: Organizations can build trust with their customers and partners by providing them with detailed information about the software components used in their products.
- Improved collaboration: SBOMs facilitate collaboration between software vendors, developers, and security researchers by providing a common language for discussing security issues.
- Enhanced compliance: SBOMs help organizations comply with regulatory requirements, such as the U.S. Cybersecurity and Infrastructure Security Agency (CISA) Software Bill of Materials (SBOM) requirements.
Real-World Examples of SBOM Usage
SBOMs are becoming increasingly important for organizations looking to improve their security posture. Several organizations have already implemented SBOMs and are seeing significant benefits. Here are some real-world examples of how organizations are using SBOMs and the challenges they have encountered.
Examples of SBOM Usage
Organizations are using SBOMs in various ways to enhance their security posture. Here are some examples:
- Software Vulnerability Management: Organizations are using SBOMs to identify vulnerabilities in their software. By analyzing the components listed in an SBOM, organizations can quickly determine which of their software products contain known vulnerabilities. This information can then be used to prioritize remediation efforts and patch vulnerable systems.
- License Compliance: Organizations are using SBOMs to ensure compliance with open-source licensing requirements. By analyzing the components listed in an SBOM, organizations can identify any open-source components that require specific licensing terms. This information can help organizations avoid potential legal issues related to open-source licensing.
- Supply Chain Risk Management: Organizations are using SBOMs to identify and manage risks in their software supply chains. By analyzing the components listed in an SBOM, organizations can identify potential vulnerabilities or security issues in third-party software. This information can help organizations mitigate risks by taking steps to ensure the security of their supply chains.
Challenges in SBOM Implementation
While SBOMs offer significant benefits, organizations face several challenges when implementing them:
- SBOM Generation: Generating accurate and complete SBOMs can be challenging, especially for complex software applications. Organizations may need to invest in tools and processes to automate SBOM generation.
- SBOM Management: Managing SBOMs can be complex, as organizations need to track changes to their software components over time. Organizations may need to develop processes for storing, updating, and sharing SBOMs.
- SBOM Integration: Integrating SBOMs into existing security tools and processes can be challenging. Organizations may need to adapt their existing security workflows to accommodate SBOMs.
Insights from Real-World Examples
The examples discussed above provide valuable insights into the benefits and challenges of using SBOMs. These insights can be applied to other organizations looking to implement SBOMs:
- Start Small: Organizations should start by implementing SBOMs for high-risk applications or components. This will help them gain experience with SBOMs and identify any potential challenges.
- Automate SBOM Generation: Organizations should invest in tools and processes to automate SBOM generation. This will help ensure that SBOMs are accurate and up-to-date.
- Integrate SBOMs into Existing Tools: Organizations should integrate SBOMs into their existing security tools and processes. This will help them leverage the benefits of SBOMs without disrupting their existing workflows.
SBOMs and Open Source Software
Open source software (OSS) is a critical component of modern software development, powering everything from operating systems to web applications. However, the very nature of OSS, with its collaborative development and widespread use, can also present challenges in terms of security and reliability. SBOMs play a vital role in addressing these challenges, providing a clear and comprehensive picture of the OSS components used in a software product.
The Importance of SBOMs for Open Source Software
SBOMs are essential for understanding and managing the security and reliability risks associated with OSS. They provide a detailed inventory of all the OSS components used in a software product, including their versions, licenses, and dependencies. This information is crucial for identifying potential vulnerabilities, managing license compliance, and ensuring the overall quality of the software.
How SBOMs Can Help to Ensure the Security and Reliability of Open Source Components
SBOMs contribute to the security and reliability of OSS in several ways:
Vulnerability Management
- SBOMs enable developers to identify and track vulnerabilities in the OSS components used in their software. By comparing the SBOM to vulnerability databases, developers can quickly determine if any of the components are affected by known vulnerabilities.
- This allows for timely remediation of vulnerabilities, reducing the risk of security breaches.
License Compliance
- SBOMs help organizations comply with the licenses associated with OSS components. By providing a clear list of all the licenses used in a software product, SBOMs make it easier to ensure that all legal requirements are met.
- This helps avoid potential legal issues and ensures that organizations can use OSS components responsibly.
Software Composition Analysis
- SBOMs are used by software composition analysis (SCA) tools, which can analyze the OSS components in a software product and identify potential risks.
- SCA tools use SBOMs to provide insights into the software’s bill of materials, allowing developers to understand the dependencies between different components and identify potential conflicts.
Supply Chain Security
- SBOMs are crucial for improving the security of the software supply chain. By providing a detailed inventory of OSS components, SBOMs enable organizations to track the origin and provenance of the software they use.
- This helps to prevent the introduction of malicious code into the supply chain and ensures that only trusted software components are used.
Best Practices for Creating and Using SBOMs for Open Source Software
Here are some best practices for creating and using SBOMs for OSS:
Creating SBOMs
- Use standardized formats: The National Institute of Standards and Technology (NIST) has developed a standard format for SBOMs, known as the Software Bill of Materials (SBOM) Standard (NIST SP 800-190). Using this standard ensures that SBOMs can be easily shared and understood by different stakeholders.
- Automate the process: Tools and platforms are available to automate the process of creating SBOMs. These tools can scan software code and automatically generate SBOMs in the desired format.
- Include all relevant information: SBOMs should include all relevant information about the OSS components used in a software product, including the component name, version, license, and dependencies.
- Maintain up-to-date SBOMs: As software evolves, it’s important to keep SBOMs up to date. This ensures that they reflect the current state of the software and provide accurate information about the OSS components used.
Using SBOMs
- Share SBOMs with stakeholders: SBOMs should be shared with all relevant stakeholders, including developers, security teams, and legal teams.
- Use SBOMs for vulnerability management: SBOMs should be used to identify and track vulnerabilities in OSS components. Tools can be used to compare SBOMs with vulnerability databases to identify potential risks.
- Use SBOMs for license compliance: SBOMs can be used to ensure that all OSS components are used in accordance with their licenses.
- Use SBOMs for software composition analysis: SBOMs can be used by SCA tools to analyze the OSS components in a software product and identify potential risks.
- Use SBOMs for supply chain security: SBOMs can be used to track the origin and provenance of OSS components, helping to prevent the introduction of malicious code into the supply chain.
SBOMs and the Role of Government
Governments around the world are recognizing the importance of SBOMs in securing software supply chains. They are actively promoting the use of SBOMs through regulations, initiatives, and programs. This section explores the role of government in encouraging the adoption of SBOMs and provides examples of government policies and programs focused on SBOMs.
Government Regulations and Initiatives
Governments play a crucial role in driving the adoption of SBOMs by enacting regulations and launching initiatives that encourage their use. These measures create a strong incentive for organizations to generate and use SBOMs, ultimately enhancing the security of software supply chains.
Examples of Government Regulations
- The United States Cybersecurity and Infrastructure Security Agency (CISA) issued a binding operational directive requiring federal agencies to submit SBOMs for all software they acquire. This directive underscores the importance of SBOMs in government procurement and strengthens the security of government systems.
- The European Union’s Cybersecurity Act mandates the creation and sharing of SBOMs for certain critical software components. This legislation aims to improve the resilience of critical infrastructure and protect against cyberattacks.
Examples of Government Initiatives
- The National Institute of Standards and Technology (NIST) in the United States has published guidelines and best practices for creating and using SBOMs. These guidelines provide valuable resources for organizations seeking to implement SBOMs effectively.
- The UK government’s National Cyber Security Centre (NCSC) has launched a campaign to raise awareness about the benefits of SBOMs and encourage their adoption across various industries.
Concluding Remarks
As software development continues to evolve, the importance of SBOMs will only grow. By embracing this technology, organizations can strengthen their security posture, improve software supply chain risk management, and gain a deeper understanding of their software’s composition. From vulnerability identification to compliance assurance, SBOMs are becoming an essential tool for navigating the complexities of the modern software landscape.
SBOMs, or Software Bills of Materials, are becoming increasingly important for security and compliance. When you’re working with an SBOM, you might need to edit the resulting PDF file, and for that, you can use a pdf editor online free.
A good online editor allows you to make annotations, add text, and even rearrange pages, making your SBOM more user-friendly and informative.
